Blue Team Basics - Local Admin Password Administration
I used to be a Domain Administrator for a large AD deployment. Centralised account and access management was always a struggle so any solution to aid the manageability of administrative credentials is a massive security bonus. I've had several people recommend this solution over the last few months so I'll do an overview of the tool for those unaware. If you're not using this then I hope you have a solution and that your solution scales well and is ultimately secure.
What is it?
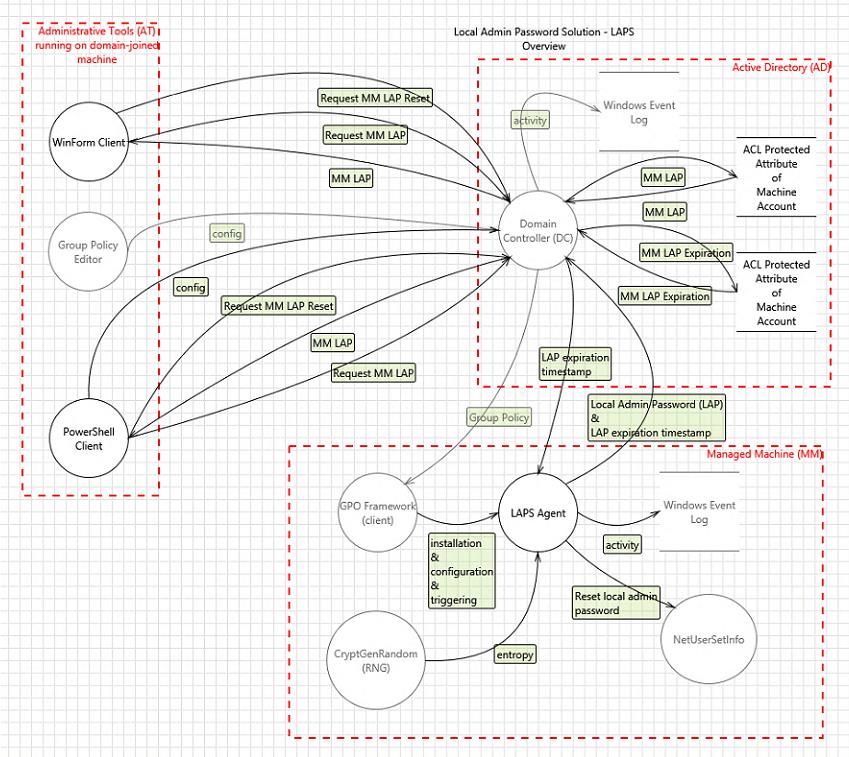
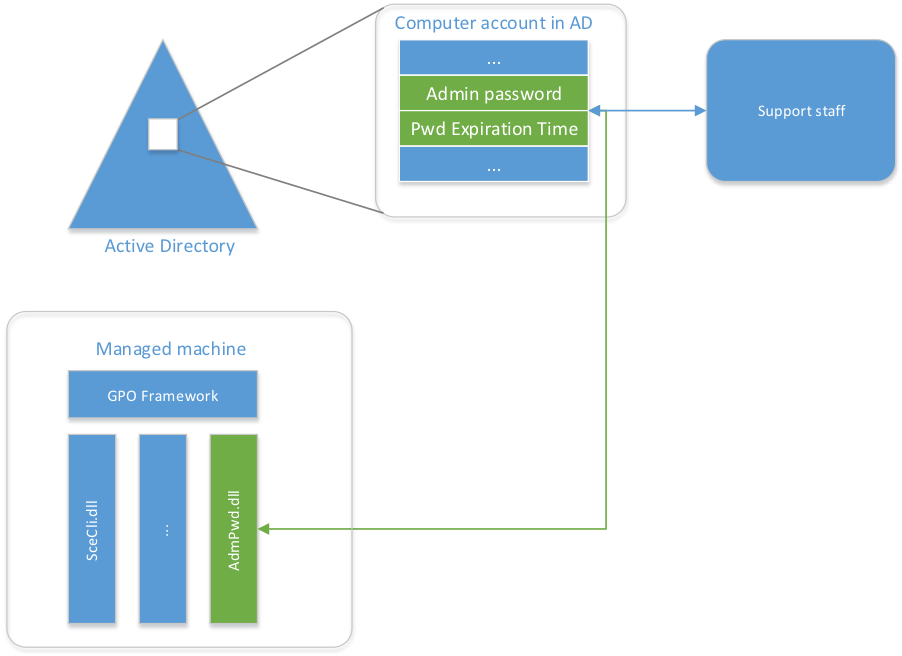
Local Administrator Password Solution (LAPS) created by Microsoft, May 2015. It's a tool for managing (domain joined) local Administrator account passwords securely inside the centralised user and account management tool we know as Active Directory.
Why you need it.
One of the problems of enterprise IT is that of password reuse of administrative accounts. One example is that numerous systems/helpdesk administrators set the same server or desktop local administrator password when building machines, this can easily abused by threat actors for lateral movement once valid credentials are gathered.
Normally in the past to get similar functionality (first hand experience here) is that you need to write a custom tool that is installed on each endpoint to manage these credentials which needs to have a backend to report the password to. This is a risky situation as any custom tool will have bugs and security implications. Another way would be to log each password into a Password Safe for each desktop/laptop/server local administration account, scaling and managing this is extremely difficult to do well.
This is one of the blue team basics no doubt. If you can manage, audit and secure your administrative accounts across your enterprise you will lower the risk of threats [1][2].
Quick Setup Overview.
The official documentation is great. Check it out here (Click Download > .docx). To quickly understand the ease of the solution;
- Upgrade AD schema to support LAPS.
- Install endpoint agent (CSE).
- Configure GPO to push LAPs policy/config.
Getting the AD schema upgrade through change management will probably be the struggle here.
Attacks against LAPS.
I have not come across any vulernabilities with LAPS at the time of writing but I will heavily recommend following ADsecurity.org hardening guides as the risk now moves ultimately to the AD infrastructure itself but also to the delegation of the LAPS AD group that can see and manage those passwords.
Passwords stored in the Active Directory are stored in confidential attributes (so as special access right is required to read the password) and protected from reading by standard Access Control List (ACL), so only users who are explicitly given the permission to read the password for certain workstation can actually read it.
Network side of things.
Transfer of password from managed computer to Active Directory is protected by Kerberos Encryption, so it is not possible to know the password by sniffing the network traffic.
Conclusions
Your eggs are all in one secure basket.
Delegation of rights to the groups that are allowed to view the passwords will need to be tighlty restricted or heavily audited. Tools like Bloodhound can be very helpful as this will paint a picture of linked groups with the goal to find the quickest route to root (Domain Admin). This will highlight abused group memberships to domain administrators that will have rights over this LAPS group no doubt.
As with any another HPA account or group; review, audit and maintain DA and LAPS groups regularly.
For further reading I'd check out https://adsecurity.org


