Multi-phish!

Social engineering is a massive attack vector for both enterprise and home users.
A friend received this crafty looking email this morning. Normally, I would just get them to check the link URL, then delete but this phish had used/guessed my name as the purchaser which was even more targeted then I'd imagine. I was glad she reported it to me first so I could check it over to see how malicious this could have been.
The email.
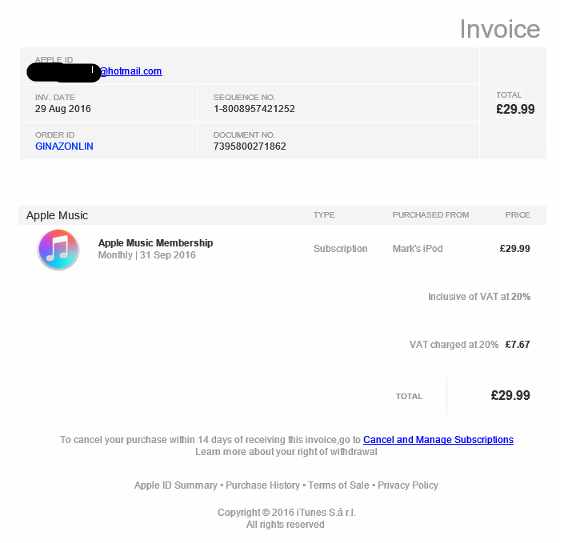

Clicking Cancel and Manage Subscriptions
hxxp://as3192.mbgotw.com/[email protected]
You have to submit an email for the redirect to work.
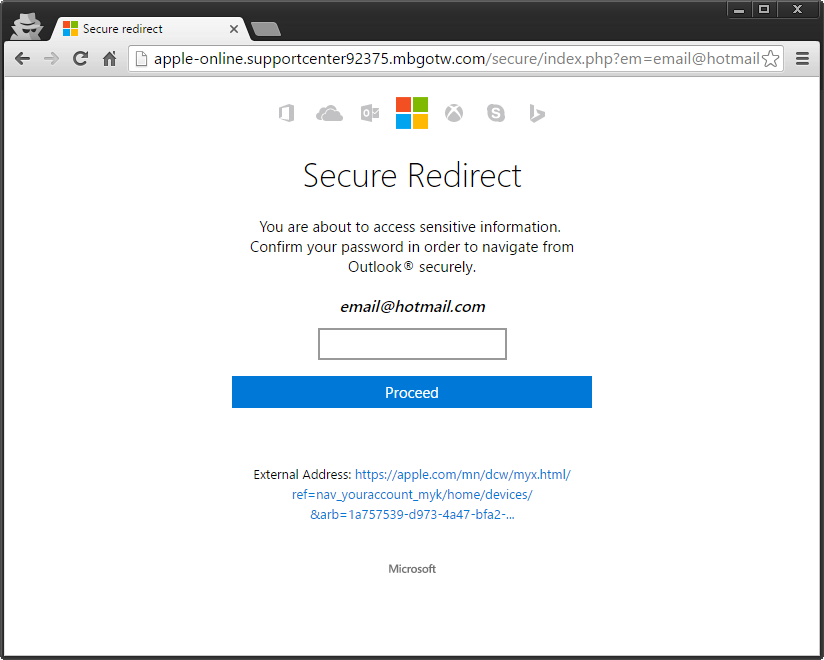
Redirects here;
hxxp://apple-online.supportcenter92375.mbgotw.com/secure/[email protected]
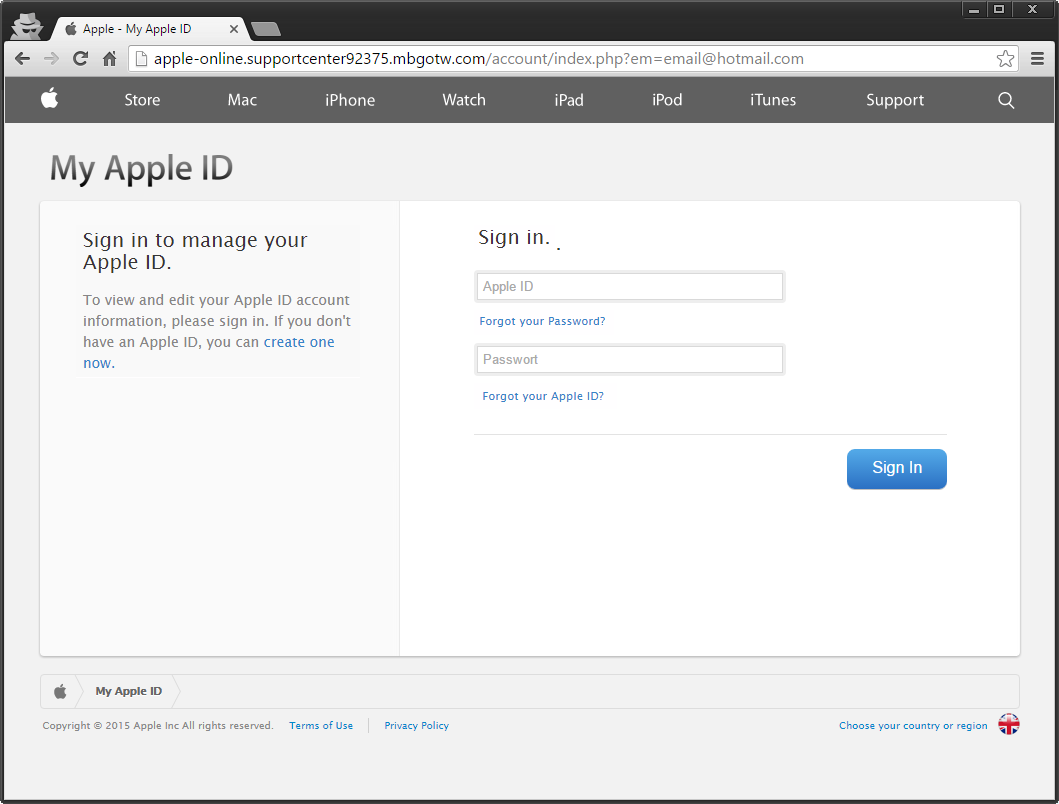
First things first, I'll have your Hotmail account please. Seems to be formatted for a phone.
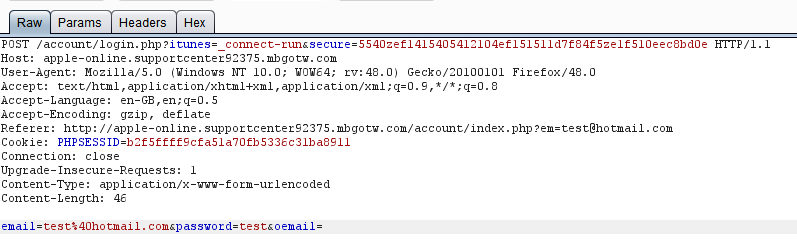
Burp submission of duff creds
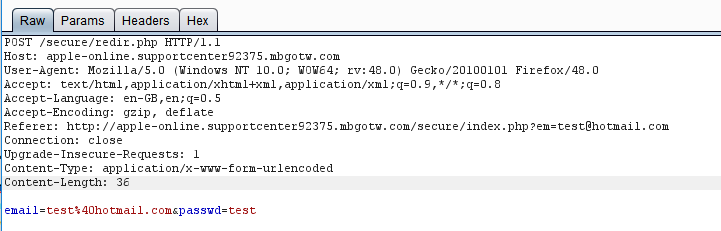
Once submitted your redirected to another page. Then I'll have your iTunes account please. Sign in!
Once it has your iTunes account details it forwards you over to a payment processing site. I need your billing details obviously!
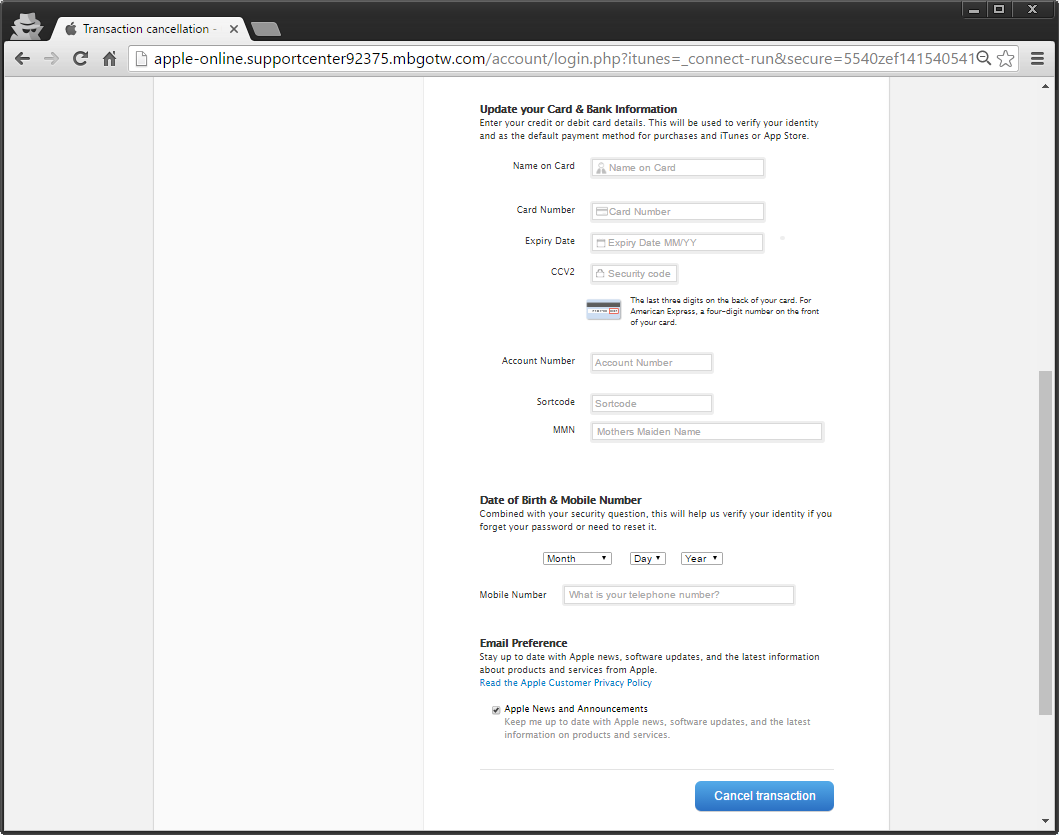
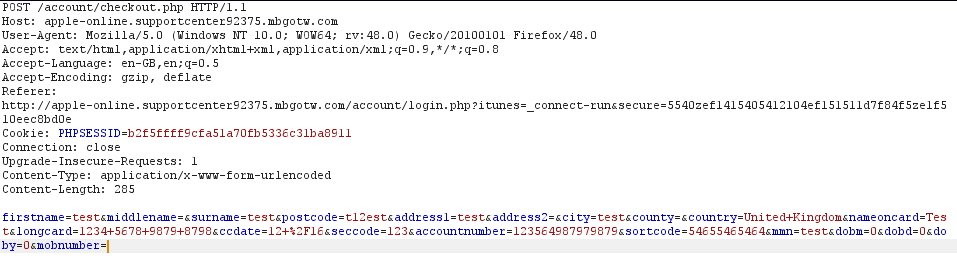
Very specific details needed...
Peter Parker, 123 Sesame Street... send.
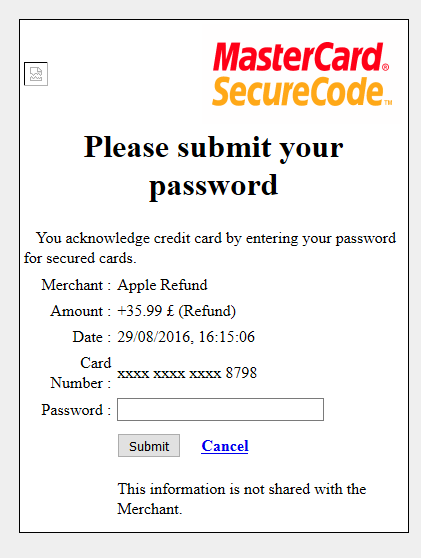
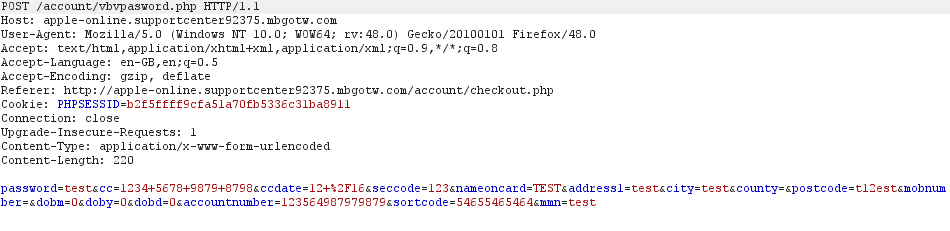
And finally, that credit card verification password. This phish really went all out.
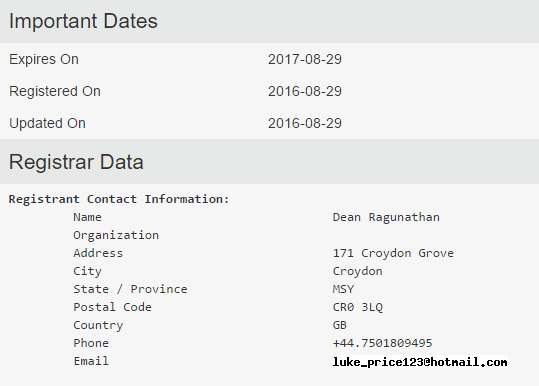
Now some quick passive recon. Standard stuff... WHOIS search

Shodan the server... https://www.shodan.io/host/217.160.0.210
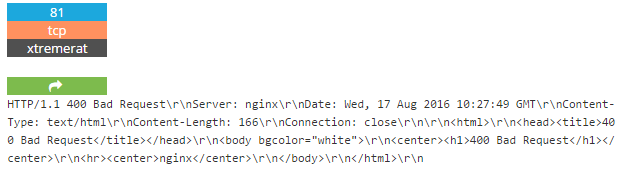
Hosting server seems to be infected with an xtreme RAT. Possibly popped server?
I felt tempted to poke but I had wasted enough time. TBC.
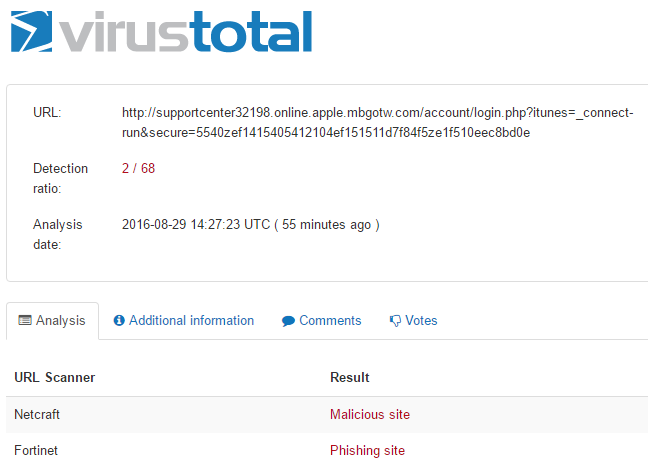
Finally, I just wanted to see if this was already on Virus Total. Only a few hits so far today.
This was a pretty nasty chained phishing attempt.

I reported the phish to Apple and sent my friend this link.
Apple's Phishing Prevention
http://www.apple.com/uk/legal/more-resources/phishing/
Advice
- Enable 2FA for all accounts that support it.
- Be cautious of any unexpected emails.
- Check all links in the email by hovering your mouse over and verifying the top level domain.
- Visit the site/service in question by typing the URL in the address bar.
- Use a SPAM filter or a browser addon (uBlock) to detect malicious sites/emails.
If unsure, report it. Ask a friend/help desk to check it out first.
Further research
These types of attacks are simple to set up. Learn form the available toolsets out there and keep teaching users on how to detect phishing emails.
SET- social-engineer-toolkit
https://www.trustedsec.com/social-engineer-toolkit/
https://github.com/trustedsec/social-engineer-toolkit